
Proxy Networks and Security: Protection Against DDoS and Brute-Force Attacks
Learn how proxy networks protect websites from DDoS and brute-force attacks, hide server IPs, and strengthen your online business security. Key benefits explained.
Proxychi
28 December 2025
459
459
28 December 2025
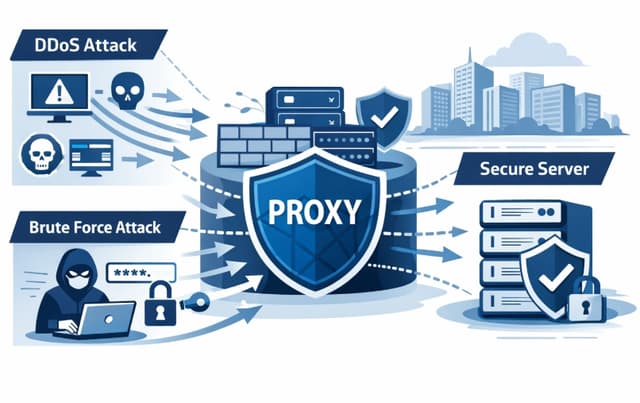
Modern websites and online services constantly face cybersecurity threats. Among the most common are DDoS attacks and brute-force attempts to crack passwords. Even a well-configured server or CMS does not guarantee full protection if your infrastructure is directly exposed to the internet. This is where proxy networks start playing a role not just as an access tool, but as a full-fledged component of a security architecture.
What Are DDoS and Brute-Force Attacks in Simple Terms
A DDoS attack is an attempt to overwhelm a server with a massive volume of requests in order to make a website unavailable to legitimate users. A brute-force attack involves large-scale automated attempts to guess login credentials for admin panels, APIs, or user accounts. Both types of attacks rely on one core principle: direct interaction with your real server IP address.
When attackers can see your infrastructure directly, they are able to:
- identify the exact attack target;
- repeat attacks from thousands of different IP addresses;
- analyze how your server responds to high traffic loads.
Why a Standard Firewall Is Often Not Enough
Firewalls and WAF solutions are essential security tools, but they operate at the server level. This means malicious traffic still reaches your infrastructure before it is filtered. During large-scale attacks, this can become a critical limitation.
A proxy network moves part of the protection outside the core server, hiding the real IP address and distributing traffic across multiple nodes. This is where the real Proxy Security Benefits become clear for businesses and online platforms.
How Proxy Networks Act as a Security Layer
A proxy acts as an intermediary between users and the server. All incoming requests pass through the proxy infrastructure first and only then reach the main resource. This approach delivers several crucial security advantages:
- Hiding the real server IP address Attackers cannot directly identify the actual infrastructure.
- Filtering suspicious traffic Requests with abnormal frequency or behavior can be blocked before they reach the server.
- Traffic distribution and load balancing Incoming traffic is spread across multiple proxy nodes, reducing the risk of overload.
Protection Against Brute-Force Attacks Through IP Rotation
Brute-force attacks are often based on thousands of repeated requests to login forms or APIs. When these attempts come from constantly changing IP addresses, traditional IP-based rate limits lose effectiveness.
This is where IP rotation becomes critical. Mobile and rotating proxies make it possible to:
- continuously change outgoing IP addresses;
- complicate traffic pattern analysis;
- reduce the efficiency of automated attack scripts.
That is why solutions built around IP Rotation Security Protection are frequently used as an additional security layer for admin panels, authentication forms, and API endpoints.
Proxies as Part of a Comprehensive Cybersecurity Strategy
It is important to understand that proxies do not replace firewalls or dedicated DDoS protection services. However, they significantly enhance their effectiveness. When combined with WAF rules, rate limiting, and traffic monitoring, proxy networks help to:
- reduce the load on the core server;
- make infrastructure reconnaissance more difficult for attackers;
- respond faster to abnormal activity;
- improve overall service stability during traffic spikes.
For SaaS platforms, eCommerce projects, marketing tools, and API-based services, this means not only better security but also consistent availability for legitimate users.
When Using Proxies for Security Makes the Most Sense
Proxy networks as a security component are especially effective when:
- the website or service exposes public APIs;
- login forms are publicly accessible;
- the project serves an international audience;
- 24/7 service availability is critical.
In these scenarios, proxies are not just a technical add-on — they become a strategic part of protecting an online business.

